Configure Identity Providers for the Management System
The Management System uses the Mosaic Identity Service to enable editors to sign in and perform their editorial work. The Identity Service supports a range of OAuth 2.0 / OpenID Connect compatible ID providers. Each of them can be configured and enabled so they could be available as a login option in the Management System.
This configuration needs to be performed in the Mosaic Admin Portal by an Administrator of the respective Tenant.
Configuring ID Providers
ID Providers can be configured through the Identity Providers station, which can be navigated through Identity Service Configuration station.
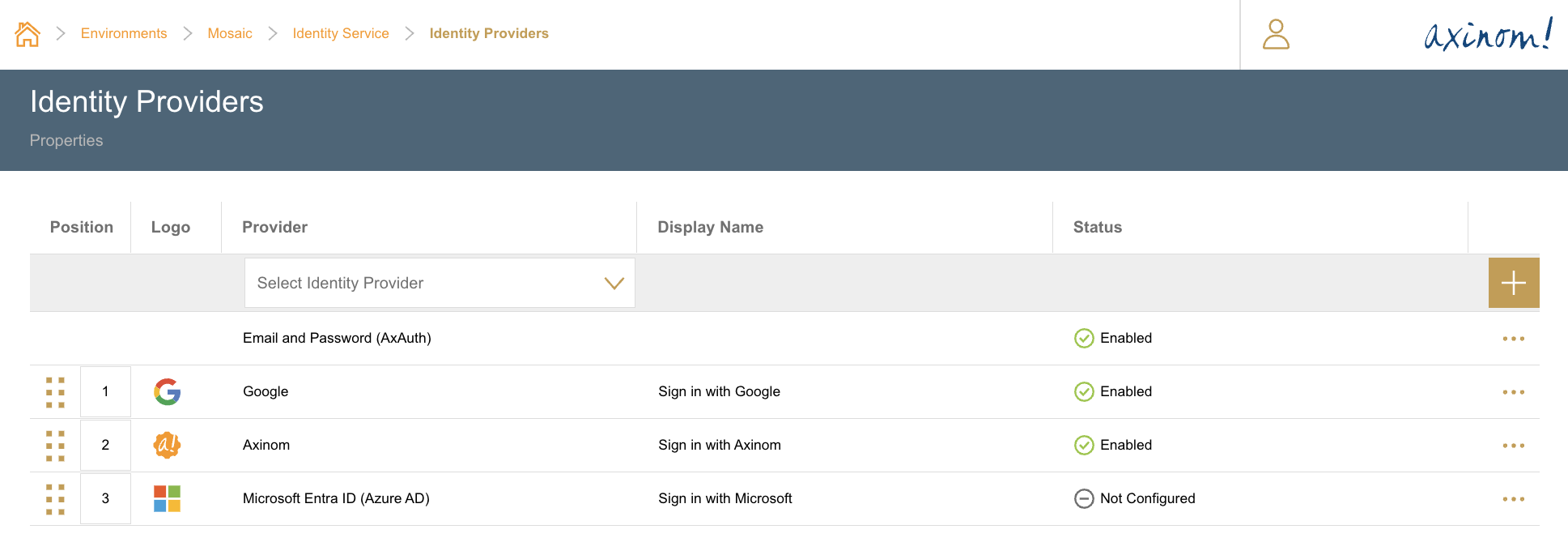
The following providers are currently supported to be configured as ID Providers for an environment.
- Email and Password (powered by Mosaic AxAuth Service)
- Axinom (Axinom Portal)
- Microsoft Entra ID (formerly Azure AD)
- Custom
Adding ID Providers to an environment
Identity Providers can be added via the + button found in the Identity Service -> ID Service Configuration -> Identity Providers station for your environment in the Admin Portal.
The sort order of the ID providers can be changed by dragging the desired row to the required position.
The immediate state of newly added ID Providers will be Not Configured. Details for each ID Provider can be viewed by clicking on the View Details inline menu.
In each detail station, configuration values for each ID Provider can be set. When the configuration is complete, the ID Provider can be marked as Enabled. Only ID Providers marked as Enabled will be shown in the Management System for user sign in.
Configuring Email and Password (AxAuth)
To configure Email and Password as an ID Provider, the environment needs to have AxAuth Service enabled. In case it is not enabled, the ID Provider will show its status as Not Available.
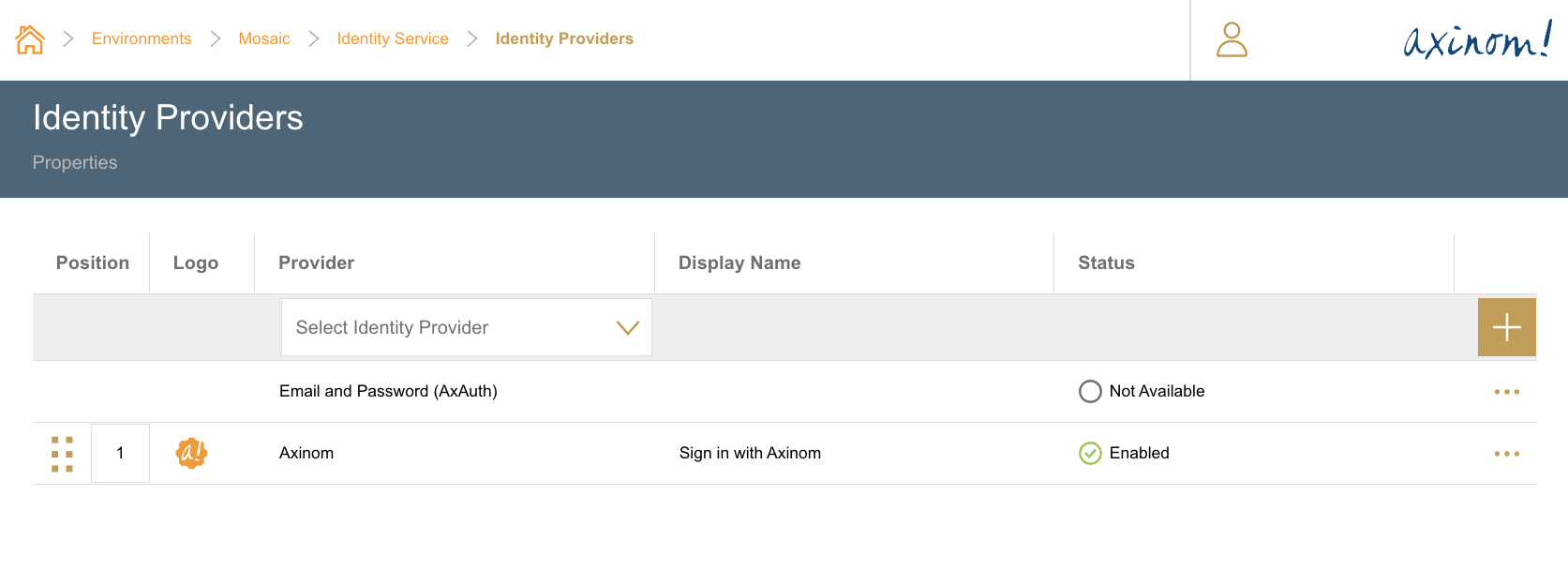
Once AxAuth Service is enabled for the environment, it will automatically configure the ID Provider and set it to enabled. The configuration includes the Client ID, Client Secret and Discovery Document URL for AxAuth.
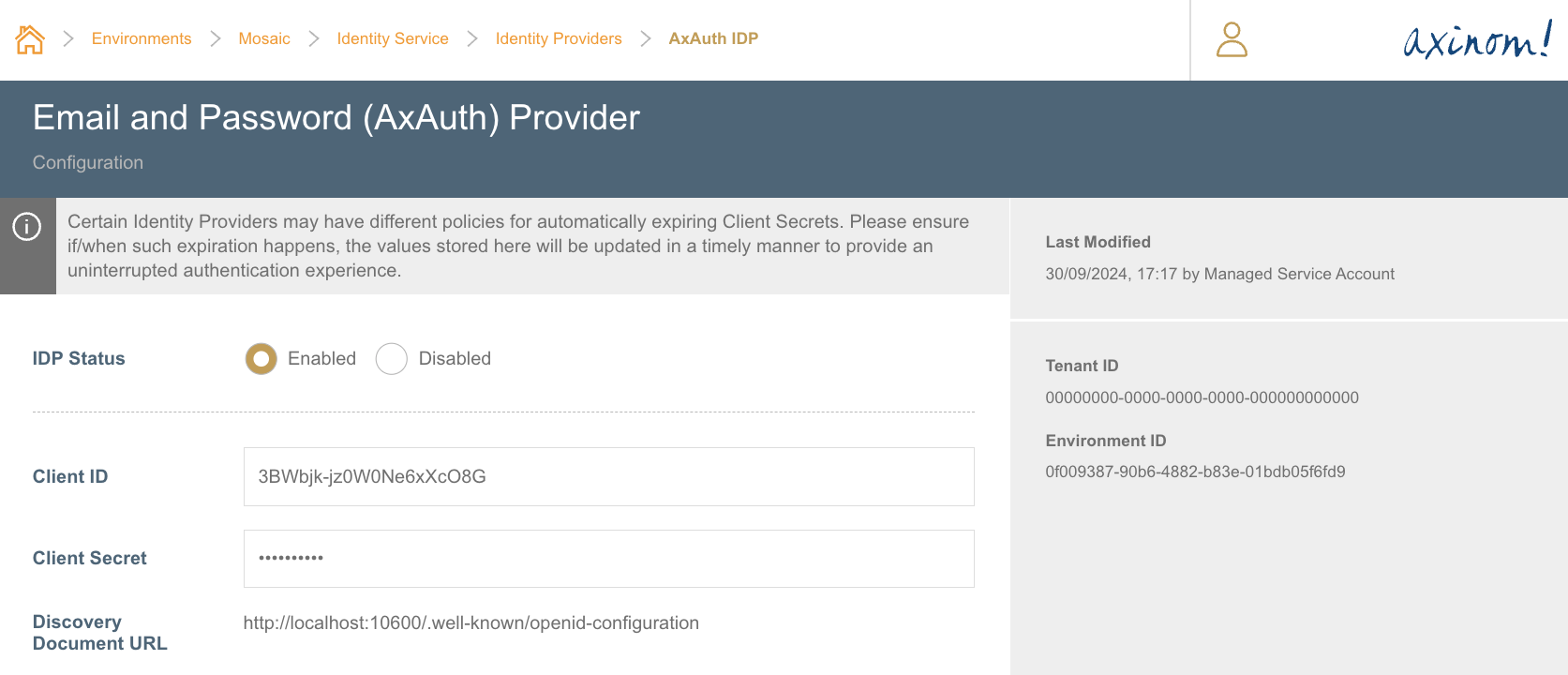
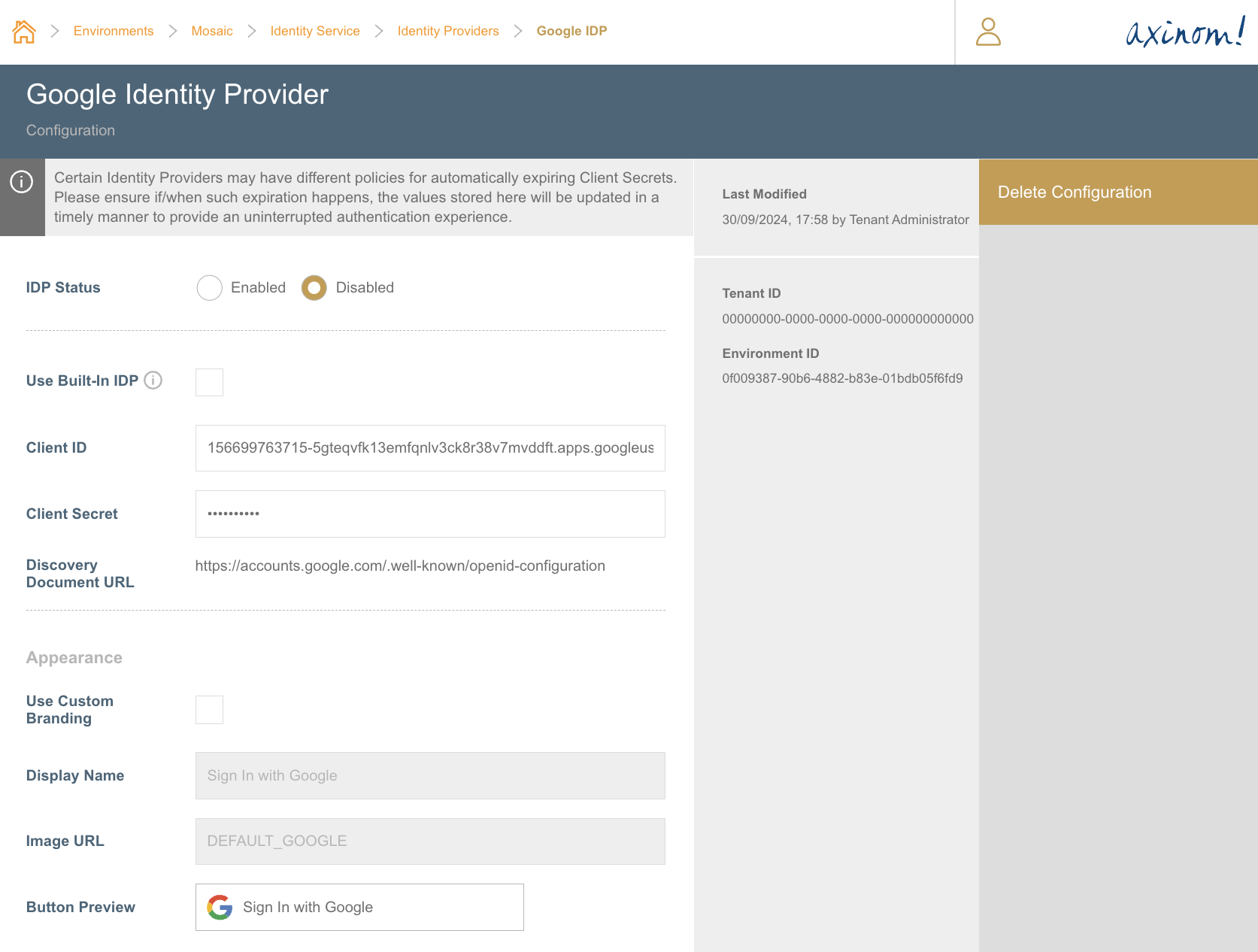
Configuring Google IDP
Google IDP can be enabled by either using a built-in Google IDP configuration or by creating a custom Google IDP configuration.
Built-in Google IDP
Google IDP will be enabled using a pre-configured Google OAuth 2.0 client which is managed by Axinom. This approach has the benefit of not having to create and maintain a Google OAuth 2.0 client on your own. Configuration settings of the OAuth 2.0 client such as authorized redirect URIs are pre-configured and cannot be altered.
Configuration
To configure Google IDP using the built-in Google IDP configuration, follow the steps below:
- Log in to the Mosaic Admin Portal.
- Locate the environment you would like to configure.
- Navigate to the Google IDP configuration station within the Identity Service Configuration.
- Select
Use Built-In IDPoption. - Once this is saved, refresh the Management System to start using the newly configured Identity Provider.
Custom Google IDP
Google IDP will be enabled using a Google OAuth 2.0 client which is managed by you. This approach gives more flexibility because configuration settings of the OAuth 2.0 client can be managed by your own.
Pre-Requisites
You first need to register a Google OAuth 2.0 client and obtain the credentials for it. You can do it directly in the Google Cloud Console. The steps are included in Google documentation.
It’s important to configure the correct Authorized Redirect URIs as they need
to be whitelisted to receive the Authorization Code from the Identity Provider.
See below for the Redirect URIs that must be allowed for the Identity Service to
function correctly.
Configuration
To configure Google IDP using a custom Google IDP configuration, follow the steps below:
- Log in to the Mosaic Admin Portal.
- Locate the environment you would like to configure.
- Navigate to the Google IDP configuration station within the Identity Service Configuration.
- Paste the
Client IDandClient Secretvalues of the Google OAuth 2.0 client created previously and save the changes. You can use the status field in the future to temporarily disable the IDP without losing the already saved information. - Refresh the Management System to start using the newly configured Identity Provider.
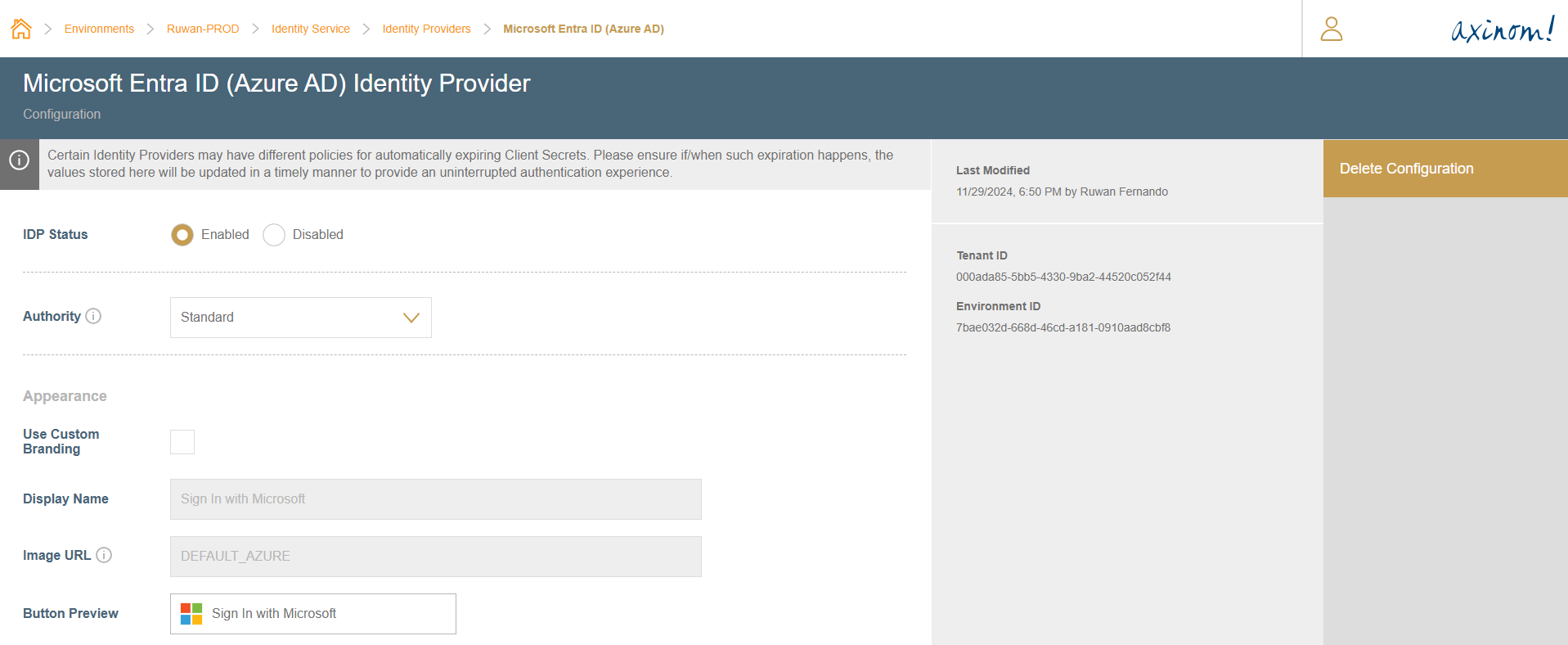
Enabling Microsoft Entra ID (Formerly Azure AD)
The Microsoft Entra ID IDP can be enabled either by using the Standard authority or the Custom authority. The difference would be, when using Standard, all users with a work or a school account from Microsoft Entra ID will be able to authenticate to the management system. Where-as when using Custom, you can be more specific about the users who are allowed to authenticate (such as on the Microsoft Entra ID users who belong to your organizations Active Directory).
Using the Standard Authority
- Log in to the Mosaic Admin Portal.
- Locate the environment you would like to configure.
- Navigate to the Microsoft Entra ID IDP configuration station within the Identity Service Configuration.
- Select
Standardoption in theAuthorityfield. - Once this is saved, refresh the Management System to start using the newly configured Identity Provider.
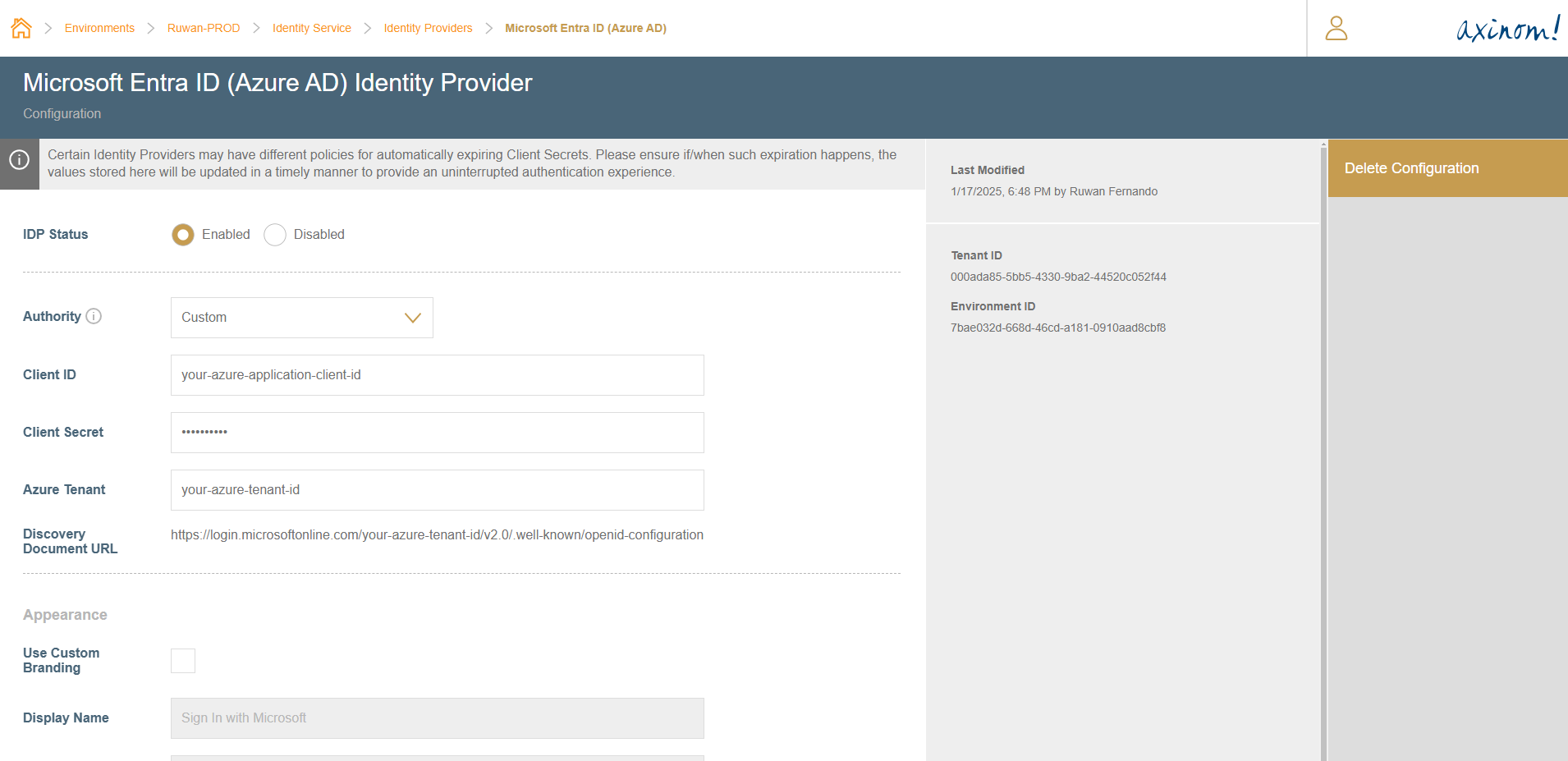
Using the Custom Authority
Pre-Requisites
You first need to register a Microsoft Entra ID Application and obtain the credentials for it. You can do it directly in the Azure Portal. The steps you then need to take are included in Microsoft Azure documentation.
It’s important to configure the correct Redirect URIs as they need to be whitelisted
to receive the Authorization Code from the Identity Provider. When choosing the
platform to configure the Redirect URIs, the Web platform must be chosen on Azure.
See below for the Redirect URIs that must be allowed for the Identity Service to
function correctly.
It is also possible to control which users and groups are allowed to log in using the AzureAD Identity Provider. You should configure this in the Azure Portal. The steps are included in Microsoft Azure documentation.
Configuration
To configure AzureAD IDP:
-
Log in to the Mosaic Admin Portal.
-
Locate the environment you would like to configure.
-
Navigate to the Entra ID IDP configuration station within the Identity Service Configuration/Identity providers.
-
Paste the
Client IDandClient Secretvalues of the Azure Application created previously. -
The value for the
Azure Tenantcan be set depending on the mode of authentication you desire as listed in the table below (the table is extracted from Microsoft documentation).Azure Tenant Description common Users with both a personal Microsoft account and a work or school account from Microsoft Entra ID can sign in to the application. organizations Only users with work or school accounts from Microsoft Entra ID can sign in to the application. consumers Only users with a personal Microsoft account can sign in to the application. Directory (tenant) IDorcontoso.onmicrosoft.comOnly users from a specific Microsoft Entra tenant (directory members with a work or school account or directory guests with a personal Microsoft account) can sign in to the application. The value can be the domain name of the Microsoft Entra tenant or the tenant ID in GUID format. -
Finally, change the
IDP StatustoEnabled. You can use the status field in the future to temporarily disable the IDP without losing the already saved information. -
Once this is saved, refresh the Management System to start using the newly configured Identity Provider.
Enabling Custom Identity Provider
The Custom IDP option can be used if you want to use an Identity Provider other than the ones that has built-in support. (i.e. Auth0 by Okta)
Pre-Requisites
You need the following information related to your custom identity provider to configure it in Mosaic.
- Discovery Document URL/OpenID Configuration URL
- Client ID
- Client Secret
If you're not sure where to find these values, please refer to the identity provider's documentation.
Configuration
Once the setup is completed in the Identity Provider, set the required credentials and OIDC Discovery Document URL along with attributes related to appearance.
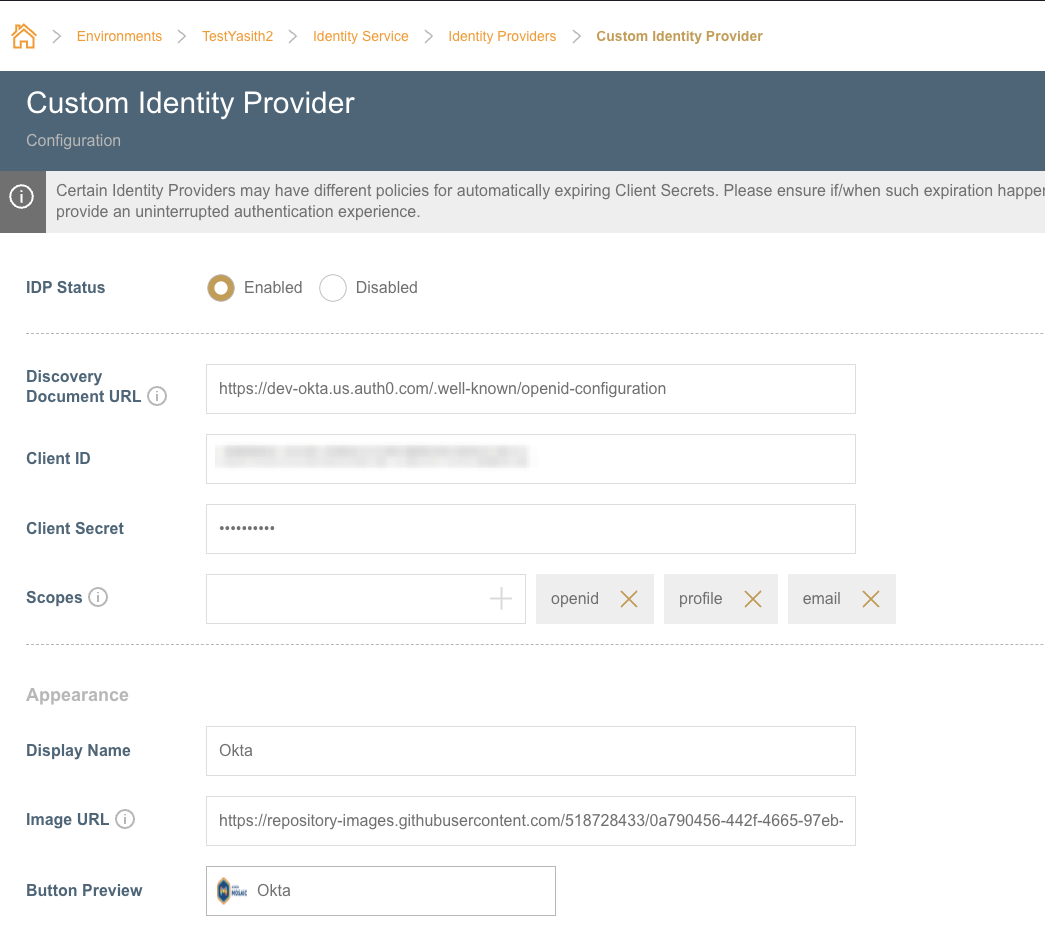
After enabling, users of the Management System will be able to sign in with the custom IDP.
Redirect URIs to be Allowed
The following redirect URIs must be whitelisted by the Identity Provider for the OAuth 2.0 Authorization Code flow to work correctly. Please consult the documentation of the respective Identity Provider to see how they can be configured.
https://id.service.eu.axinom.net/auth/callbackhttp://localhost:10505/auth/callback- The localhost URL is only needed if you intend to run the Management System workflows on your localhost, such as for development purposes. It is recommended not to use this URL for other purposes.
See also:
Custom Branding Options
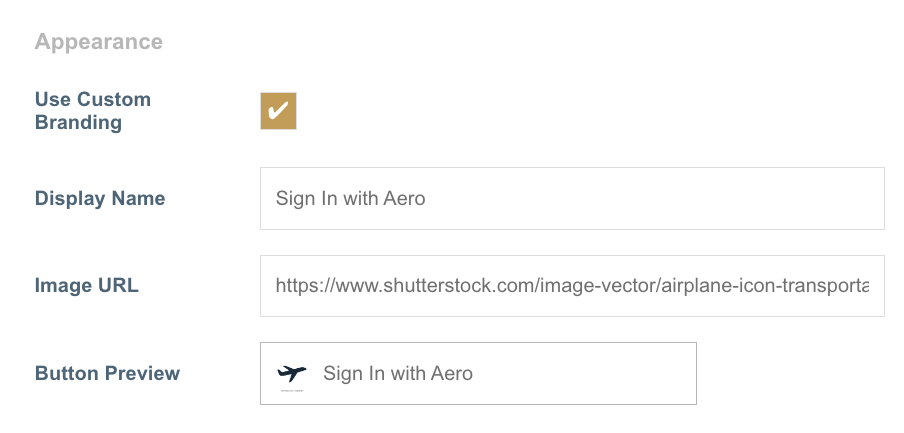
For Google and Microsoft Entra ID, Mosaic gives the ability to customize the look and feel the editors will get when signing in to the management system.
In the Appearance section, when the Use Custom Branding checkbox is checked, the Display Name and Image URL fields will become enabled.
Here, you can give the text that will appear in the sign in button for the respective ID provider and a URL for the icon that needs to appear. The Button Preview will show how it will appear in the Management System sign in page.
You can go back to the default settings by unchecking the Use Custom Branding checkbox.